Jumpbox or Bastionhost are thing of the past. The new way of giving controlled access in GCP is via IAP
Scenario #1:
Bob is an IT admin who is trying to access company ABC's secure server

Problem: Exposing a secure server to the internet increases attacks by hackers.
Solution : Add one more server known as a Bastion Host or Jump Servers in front of the secure server.

Better Solution: If your underlying Cloud Strategy is Google Cloud Platform use IAP - Identity Aware Proxy.
First lets understand SSH!
SSH is a network protocol that gives us the ability to access a computer over an unsecured network in a secure way. In addition to this, SSH provides strong password and public key authentication, along with encrypted data for communication between two computers that may be connecting over the internet or otherwise.
SSH typically runs on port 22.
If you have seen any movie on hacking and the guy types away on a black screen with the green font - you guessed it! they are using SSH or at least pretending to ;-)
What is IAP?
Now that we understand the SSH and the concept of tunneling. Let's look at IAP (Identity Aware Proxy), it uses TCP forwarding to connect to servers on GCP which don't have public-facing IP addresses. Let's look at the diagram below to visualize the architecture.
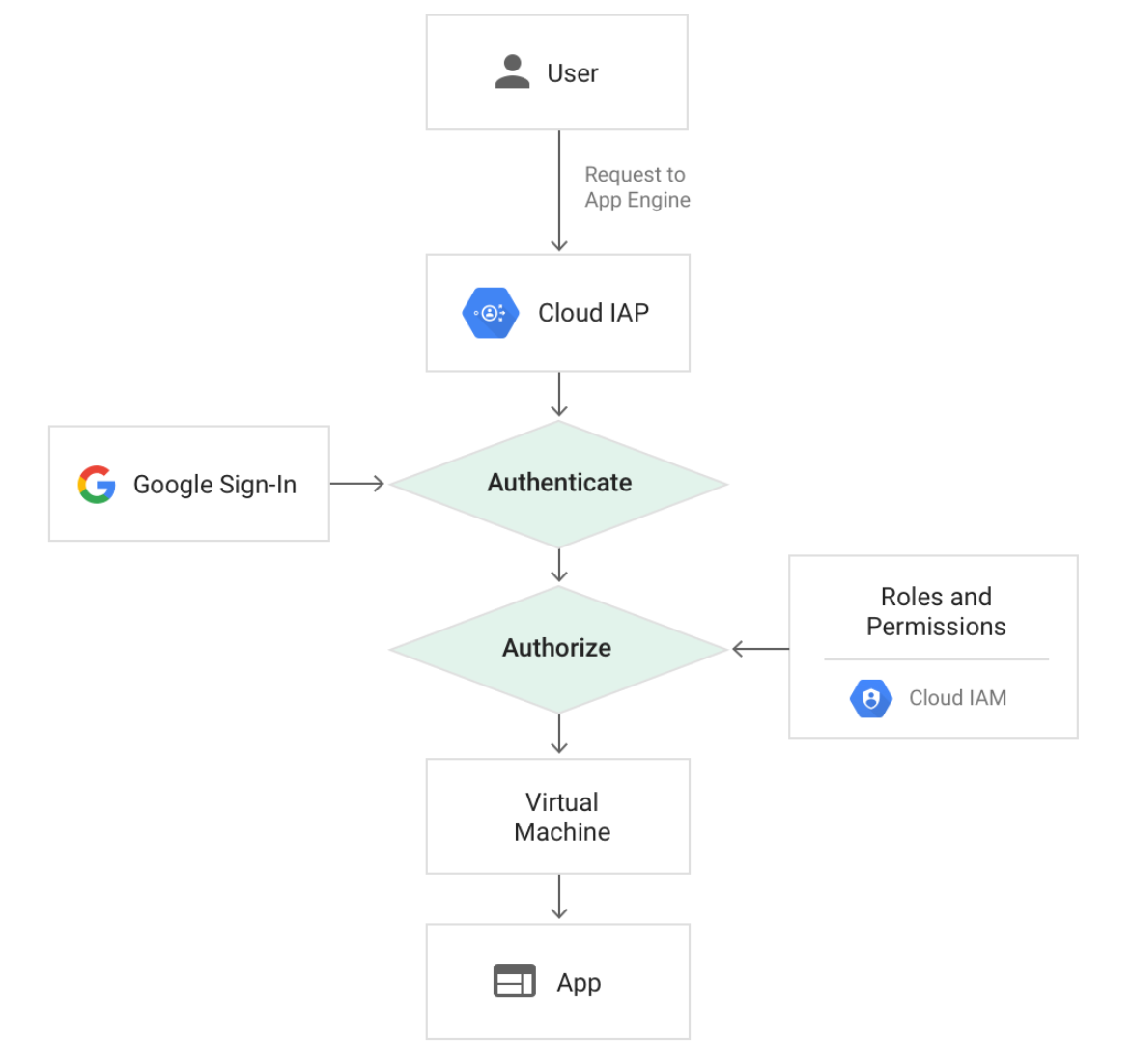
IAP acts as a middle man, which will validate a user's access levels and credentials before letting them into the server via SSH. This added layer of security removes the need to host and manually manage a Bastion host or jump box. The "gcloud cli" tool will manage the keys required for private-public encryption in SSH.
How to setup IAP in GCP?
Step 1 - Ensure that your VM (Compute instance or equivalent) is running.
Step 2 - Go to GCP console --> IAM Roles and Permissions, select your user id and the role iap.tunnelResourceAccessor
In your terminal or gcloud CLI run the following commands
Step 3 - Add required IAM permissions to your project & user id
gcloud projects add-iam-policy-binding <project id> \
--member=user:<your email id> \
--role=roles/iap.tunnelResourceAccessor
This command will add role -
iap.tunnelResourceAccessorto the user account in the project id
gcloud projects add-iam-policy-binding <project id> \
--member=user:<your email id> \
--role=roles/compute.instanceAdmin.v1
This command will add role -
compute.instanceAdmin.v1to the user account in the project id
gcloud projects add-iam-policy-binding <project id> \
--member=user:<your email id> \
--role=roles/iam.serviceAccountUser
This command will add role -
iam.serviceAccountUserto the user account in the project id
Replace <your email id> & <project id> with your GCP email id
The above gcloud commands will bind the IAM policies which will allow the GCP account user to access SSH tunnel via IAP for the specified GCP project id.
Step 4 - Allow incoming IAP requests for SSH
gcloud compute firewall-rules create allow-ssh-ingress-from-iap \
--network=<my-private-vpc> \ # defaults to network - 'default'
--direction=INGRESS \
--action=allow \
--rules=tcp:22 \
--source-ranges=35.235.240.0/20
Replace <my-private-vpc> with your vpc name
This command will add firewall permissions to allow port 22 (i.e. default SSH port) and the source IP range of GCP IAP tunnel service (the IP range is mentioned in the official documentation)
Setp 5 - SSH into the server using gcloud
gcloud beta compute ssh \
--zone "<us-central1-a>" "<my-instance>" \
--tunnel-through-iap --project "<project id>"
replace "<tags>" with relevant values
- Zone
- Instance name
- Project ID
Voila! you have successfully SSH-ed into the server
Summary
In this post, we looked at the following topics -
- Access the secure server using SSH
- SSH tunneling in GCP using IAP
In the next post, we will learn how to configure the Cloud NAT service to bring internet connectivity to our servers in the private network.
There is a lot of stuff that we couldn't cover in the scope of this article but feel free to go through the references given below. We hope you had fun reading it as much as we had fun writing it!
References










Join the conversation